
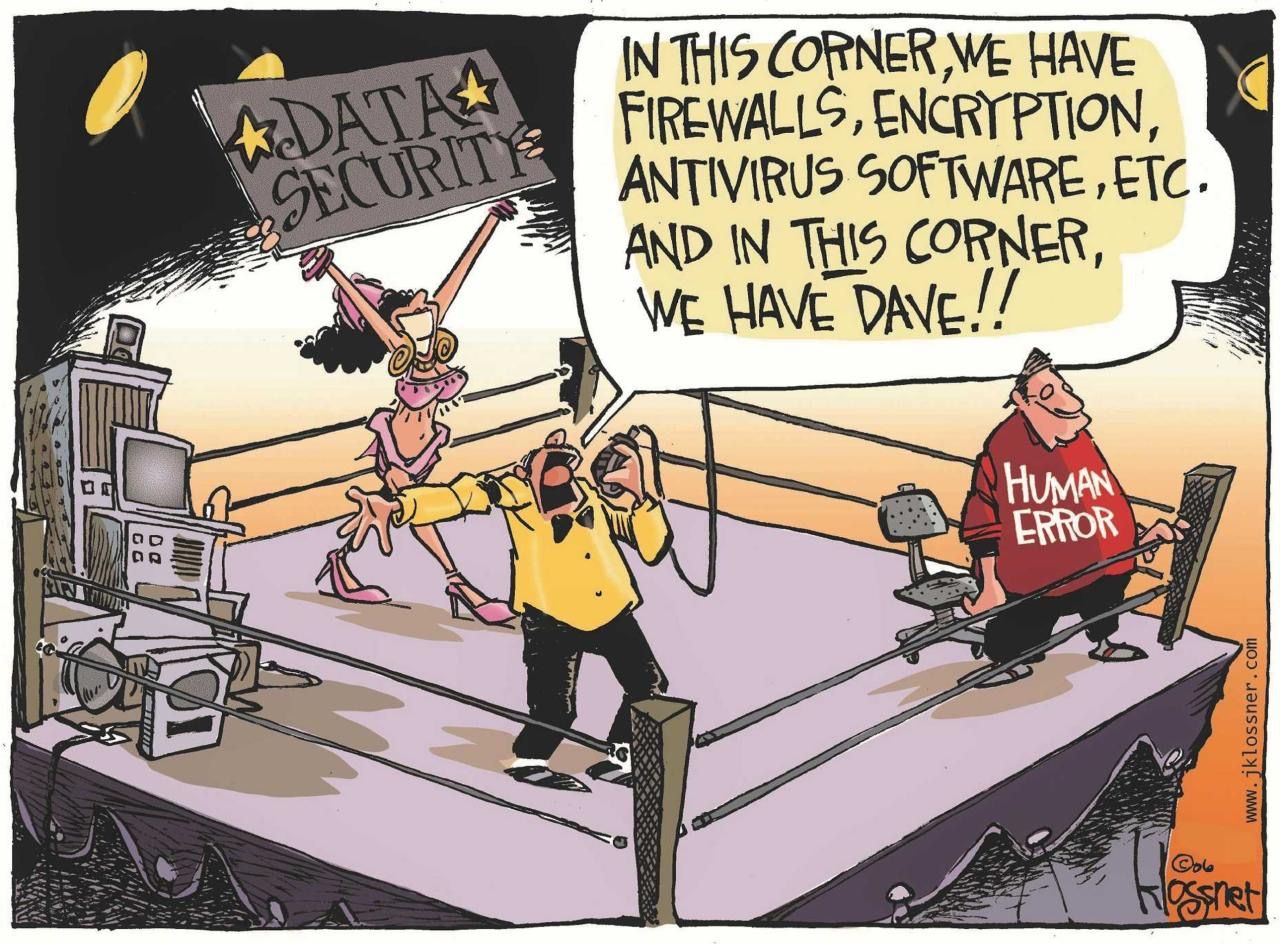
Enough said…
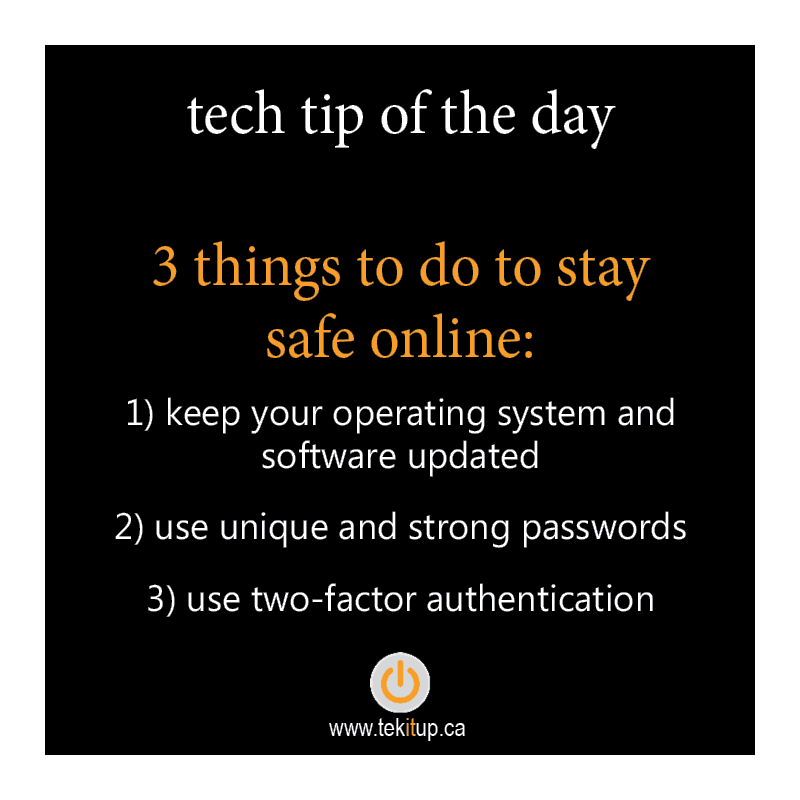
Posted by Marco Hernandez | Oct 19, 2020 | Cybersecurity | 0 |


Established in 2008, TEK IT UP has been serving small businesses and residential customers in the Greater Toronto Area.
We understand the technology challenges entrepreneurs face daily and we have made our mission to provide fast, reliable, and affordable I.T. services and consulting



